White-hat ISP turned malicious?
Back in 2015, while Mark Zuckerberg was busy announcing that Facebook had passed a billion users, an IBM company, SoftLayer, was experiencing huge increases in Spamhaus listings.
SoftLayer was known to be a responsible internet service provider (ISP). However, towards the end of the year in question, they had reached the dizzying (and depressing) heights of being #1 on Spamhaus’ Top 10 List for most abused ISPs.
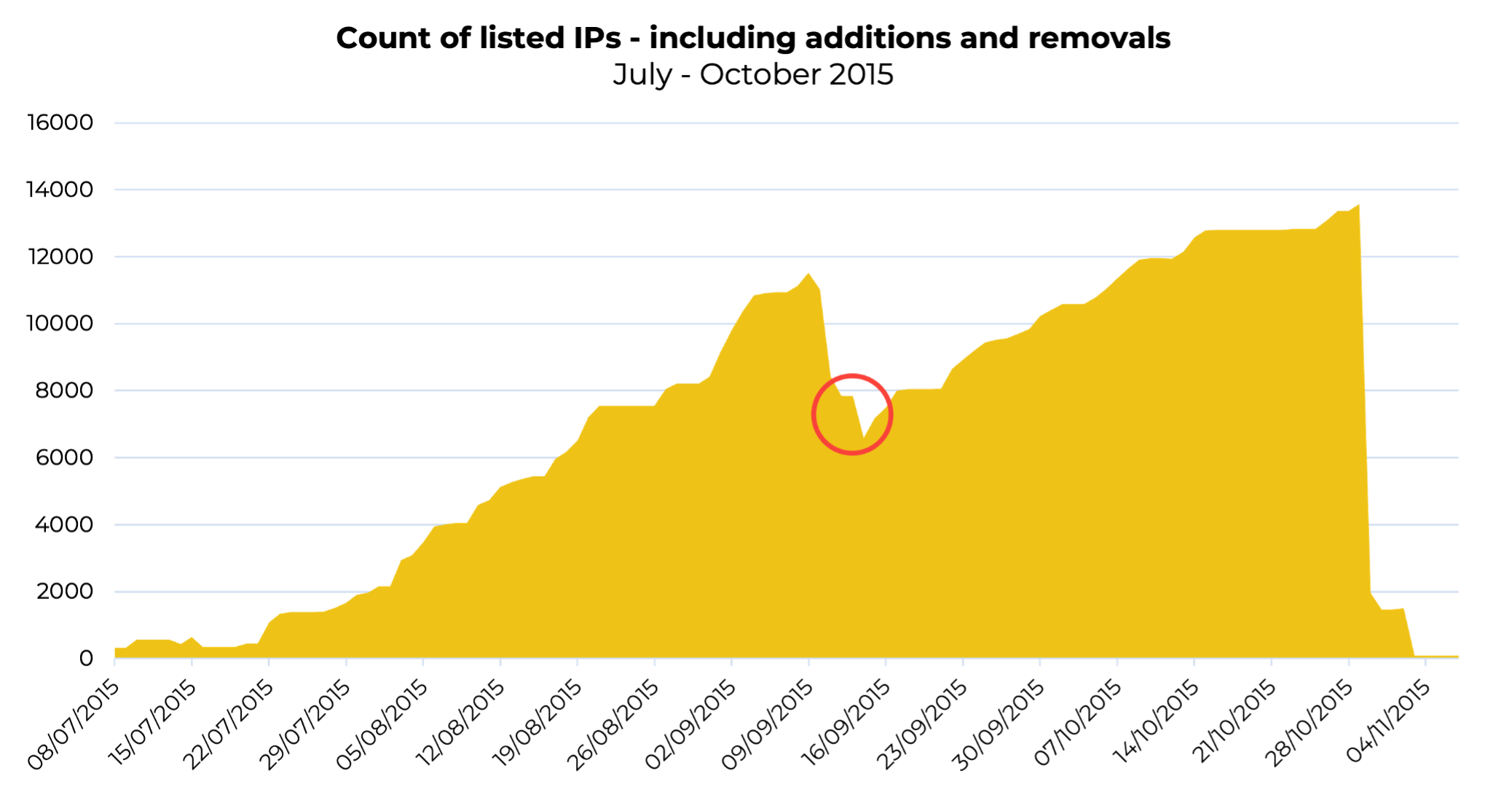
Let’s quantify “huge increases”; these were the days when responsible ISPs would hover between 20-200 listings at most; anything over this would point to you being an irresponsible network. From the chart below, you’ll see SoftLayer’s listings were breaking 12,000 at their peak. At the time, this struck our researchers as unusual. What was going on at SoftLayer? Why had this white-hat ISP suddenly turned rogue?
Uncovering the underbelly of a focused malware gang
Spamhaus researchers investigated, and it became evident that this proliferation of listings was the result of the following activity:
- SoftLayer IPs were being used to send malspam (lots of it).
- The emails used in these spam campaigns had been harvested from users across the globe, but…
- The targets of these campaigns were specifically Brazilian users.
- The campaigns tricked the Brazilian victims into downloading and installing malware.
No sooner had our researchers established the names of the companies assigned to these abused IP address ranges than they would reappear in use by a different company. Except it wasn’t a different company. It was the same people sending the same malware. This occurred daily. Sometimes, these fake but plausible Brazilian company names would change several times daily!
SoftLayer quickly responded to Spamhaus’ abuse reports, but as soon as the ISP had remediated the reported IP addresses, they were rapidly re-assigned to the same malicious operator. The situation was quickly escalating into a frantic game of whack-a-mole.
The red circle in the above chart indicates the point that SoftLayer initially thought they had gotten a handle on the situation, with listings starting to decline, before once again rising. At this point, Spamhaus decided to stop removing listings until SoftLayer took action to ensure this wasn’t going to continue.
And that action was?
Blocking port 25.
For years, Spamhaus has recommended that ISPs disable port 25 on routers and firewalls. This doesn’t prevent mail software from working normally; however, it does prevent abusive connections from leaving an ISPs network. Read more in this FAQ.
Only a few years ago, Spamhaus worked with Amazon, who were struggling with abuse on their network, and resolved the issue by blocking port 25.
Once SoftLayer took this action, its listings fell off a cliff, as the above chart illustrates! As to why this ISP suddenly became this operation’s place of choice to host its malspam operations, we can’t be 100% certain. Nevertheless, we strongly suspect that it came down to a relaxation in vetting procedures (the reason in most cases of fraudulent registrations). Perhaps SoftLayer was trying to grow rapidly in the Brazilian market.
Alls well that ends well?
Sadly, no. While SoftLayer has not experienced another crisis with listings, the operation in question is alive and kicking and continuing to target Brazilian users.
While their activity ebbs and flows, which is often the case with bad actors, their modus operandi has remained constant, using banking trojans alongside phishing tactics to target Brazilian banks.
Ways of working
Usually, this operation sends from dedicated IPs using dedicated, throwaway domains for hostnames. More recently, we’ve seen a handful of campaigns using hostnames in dynamic DNS resources; take DynDNS, for example.
This malware operation is prudent in ensuring the reverse DNS (rDNS) matches the hostname it uses for the sending. In the case of the DynDNS resources, the direct DNS resolution for the hostname itself lasts only for the duration of the sending campaign: once the sending is over, the hostname also ceases to exist. This makes it more difficult to identify resources before the sending commences, making the defense against these operators purely reactive.
The human impact
This malware gang (on the whole) expertly creates content that appears legitimate in the form of invoices, fines, and even court documents – intentionally targeting communications that would trigger worry, provoking victims to open the content. These tactics make it exceptionally difficult for anyone who isn’t a cyber expert to distinguish between the real things.
Meanwhile, the financial impact of a banking trojan can be ruinous for the victim. In the worst-case scenario, cybercriminals can gain full access to the victim’s bank accounts and money. For most banks in Europe and the US, if you fall victim to a trojan, you are responsible, and the bank will not support you.
Sadly, the operations of this malware outfit are showing no signs of abating.