Cake and DNSBLs – here’s what they have in common
Anyone who has attempted to bake a cake will tell you that you can’t “wing-it.” Ingredients need to be carefully measured and mixed in a specific order. Otherwise, you’ll have a sub-optimal outcome, or in my case, something that resembles a brick!
The same is true for the order in which you use our DNSBLs; apply the wrong DNSBL to the wrong part of the email filtering process, and you’ll have a sub-optimal filtering outcome. On the flip side, combine the right DNSBLs at the right stage of the filtering process, and you will maximize your catch rates, increasing network, and end-user protection.
Where to apply Spamhaus DNSBLs
We are assuming that your knowledge of email source code is sound; however, if you need a refresher course, look at this post, which takes an in-depth look at the code.
In the meantime, the table below details different email elements. Each element is associated with the relevant DNSBL to use with it. In addition to this, we highlight which SMTP phase this is associated with.
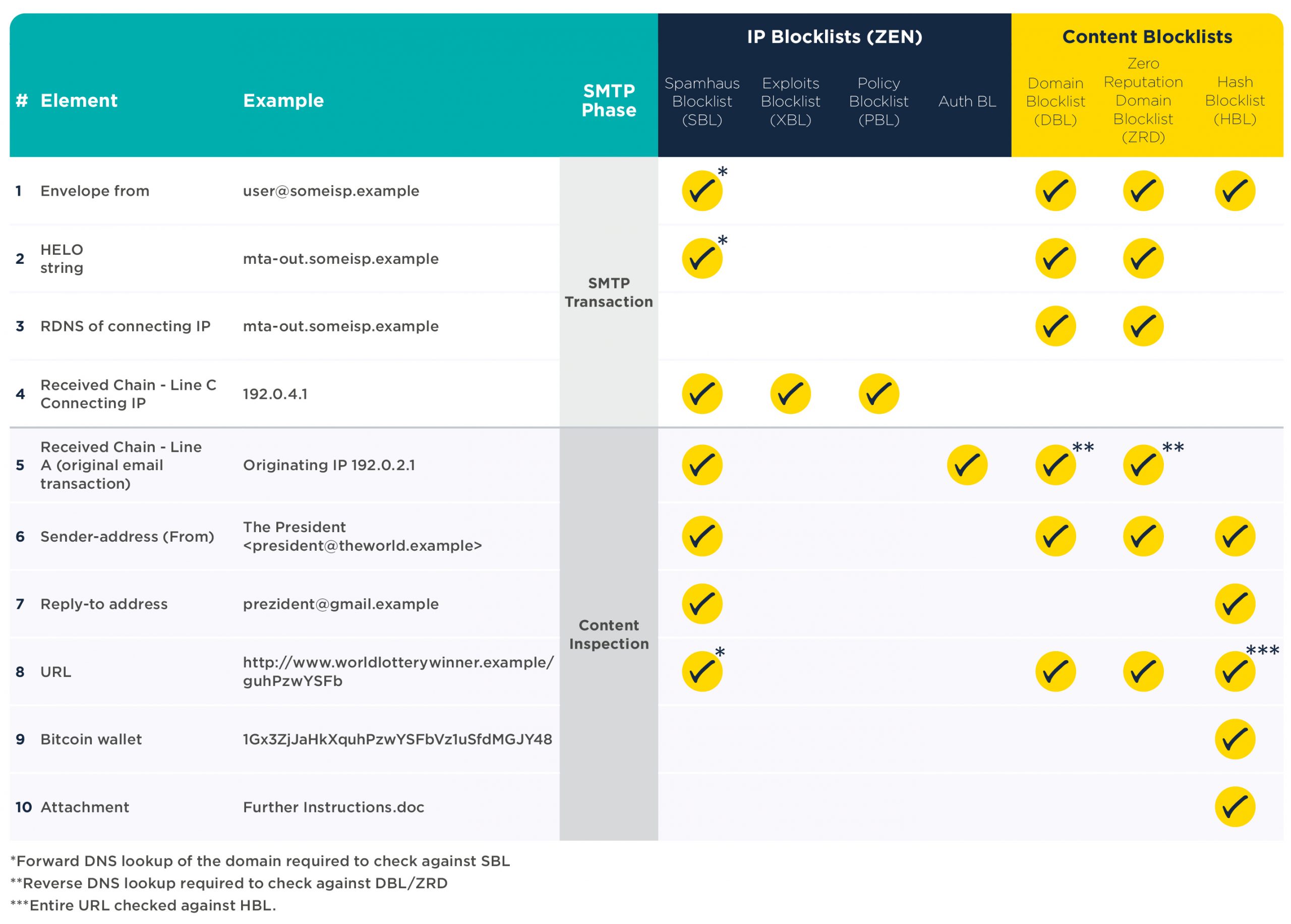
The benefits
By using Spamhaus DNSBLs at the right point in the email filtering process, you can block a huge percentage of unwanted emails at the SMTP handshake, and then weed out additional email threats throughout the content filtering process. This technique has been proven to save companies not only money on infrastructure costs and expensive email filtering solutions, but also man-power costs…and let’s not forget the ultimate aim – keeping their users and networks safe.