Quick introduction to Passive DNS data
Passive DNS utilizes anonymized query data, collected from recursive DNS servers worldwide. It collects various record types including: IPs, domains, hosts, name servers, and canonical names. This data allows us to map the connections between these different internet records, providing valuable insights into DNS activity.
The Research: Examining Newly Registered Phishing Domains at Scale
Over a ten month analysis period, 15,000+ domains were analyzed, tracking the ever-evolving tactics of phishing adversaries, focused on:
- infrastructure abused by criminals to host newly created phishing domains,
- brands impersonated by cybercriminals,
- patterns of malicious/suspicious activity linked to infrastructure, and,
- lifespan of phishing domains before they become inactive.
Find the full research paper here.
Using Spamhaus’ Passive DNS API
Four key areas of research were investigated using the Passive DNS tool. Below is an outline of how Passive DNS helped uncover patterns of suspicious and malicious behavior and the key findings:
Use case 1: The historical activity of domains
Passive DNS records historical IP addresses that a domain has resolved to by referencing DNS traffic on the internet. Researchers used the tool to identify the first and last timestamps of when an IP was assigned to a domain. Reverse IP lookups on specific IP addresses revealed the domains and corresponding hostnames they hosted over a 12-month period. This analysis uncovered the top ten Autonomous Systems (AS) abused to host phishing pages across more than 15,000 domains.
Use case 2: Do autonomous systems (ASes) collude with criminals?
Previous research [1, 2] has shown that certain ASes collude with criminals, enabling illicit activities such as phishing. These ASes are often referred to as bulletproof hosting providers [3]. In one case, the Passive DNS tool helped uncover that four identified IP addresses within a newly registered IP range of a particular AS hosted over 6,000 suspicious domains within a 12-month period. This suggests that the AS is either failing to proactively monitor content hosted on its servers or is knowingly facilitating illicit activity. Criminals use brand names in the domain name to lure victims. Researchers identified the most popular targeted brands by analyzing the domain names - see the following chart and table: 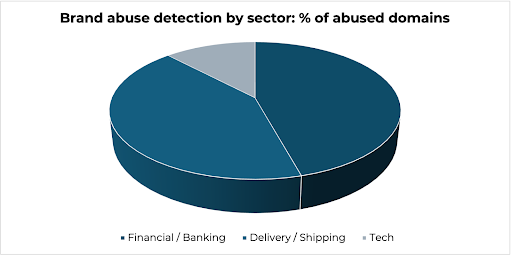
| Brand | Sector | Number of Domains |
|---|---|---|
| Royal Bank of Canada | Financial/Banking | 1,268 |
| Royal Mail | Delivery/Shipping | 1,015 |
| Santander | Financial/Banking | 916 |
| DHL | Delivery/Shipping | 889 |
| Apple | Tech | 775 |
| EVRI | Delivery/Shipping | 702 |
| An Post | Delivery/Shipping | 97 |
| Barclays | Financial/Banking | 277 |
| Deutsche Bank | Financial/Banking | 240 |
| AIB | Financial/Banking | 229 |
While this research looks into the brands targeted by the initial 15k domains, the new domains and hostnames identified using passive DNS can further help identify brands that criminals impersonate to lure victims into phishing.
Use case 3: How long are the domains active?
The Passive DNS tool was used to collect IP addresses and identify the ASes abused by criminals to conduct phishing. Additionally, it provided timestamps indicating when an IP address was first observed in association with a domain. Analysis revealed that criminals often abuse domains as soon as they are registered by deploying phishing websites.
It’s a 48 hours business model
Using Passive DNS, analysis revealed that 89.45% of domains were active for less than two days, while only 6.59% were active for more than 15 days. The tool also helped determine the closest date between Spamhaus first seeing a domain and the latest TLS/SSL certificate issued.
So, what can we learn?
Identifying newly registered domains used solely for phishing, allows for their quick addition to blocklists. Unfortunately, growing competition among registrars, the availability of multiple top-level domains (TLDs), and easy access to protective DNS services - such as Cloudflare - are making it easier for criminals to register and operate domains. Furthermore, these factors can often complicate efforts to block IP addresses, hindering takedown companies from blocking these sites. In many scenarios, blocking domains and hostnames on the DNS level can mitigate that attack vector.
Supporting the research community
The initial findings of this research underscore the crucial role Passive DNS can play in uncovering malicious activity patterns and informing effective mitigation strategies. By equipping researchers with powerful tools like Passive DNS, we continue to support the fight against online threats and advance our shared mission to strengthen trust and safety on the internet.
Would you like to use Spamhaus' data in your research?
If you’re part of a research team, and want to learn how to access Spamhaus’ IP and domain reputation data to support your work, contact us here.
References: [1] A. Noroozian, M. Korczynski, S. Tajalizadehkhoob, and M. van Eeten, “Developing security reputation metrics for hosting providers,” in 8th Workshop on Cyber Security Experimentation and Test (CSET 15), 2015 [2] C. A. Shue, A. J. Kalafut, and M. Gupta, “Abnormally malicious autonomous systems and their internet connectivity,” IEEE/ACM Transactions on Networking, vol. 20, no. 1, pp. 220–230, 2012. [3] D. Mahjoub, “Behaviors and patterns of bulletproof and anonymous hosting providers,” Usenix Enigma’17, 2017.